Dear Doc: In the United States, you can register just about any trademark on just about anything. Marks that are not okay in foreign countries (like place names such as “champagne”) are routinely used and registered in the USofA. Why, then, did the Supreme Court nix registration of the mark “Trump Too Small”? Signed,Rube Marko […]

Blog – Adam Garson Law
Nibbled to Death by Ducks
If you are a small business person, then this article is for you. A new Federal law called the ‘Corporate Transparency Act’ (CTA) goes into effect at the end of this year. The CTA was first enacted in 2020 for the purpose of combatting money laundering. “But wait,” you say, “I’m a small business person. […]
Chili Crunch Gives Momofuku Heartburn
Policing trademarks is as important as registering them. Policing requires that you monitor the world of commerce to ensure that others are not using your marks — or confusingly similar marks — and, if so, that you take immediate action against the infringers. There is little point in owning a trademark if you are willing to […]
In our experience, trademark applicants are often confused about the specimen requirements submitted with a trademark application involving goods (as opposed to services). The specimen is used to prove “use in commerce.” Use in commerce under the Lanham Act is deemed to be when the mark is “placed in any manner on the goods or […]
In last month’s newsletter, we wrote about a proposal by the U.S. Department of Justice (DOJ) to transfer marijuana from Schedule I to Schedule III. Under the Controlled Substances Act (CSA), Schedule I substances are considered to have no currently accepted medical use and a high potential for abuse. Possession and sale of cannabis is […]
Cannabis Scheduling and Rescheduling: Part I
Another Long Strange Trip In 1970, the U.S. Congress enacted the Controlled Substances Act (CSA) to establish a federal drug policy regulating the manufacture and distribution of regulated substances. The CSA classified cannabis (the CSA schedule refers to marijuana and cannabis interchangeably.) as a Schedule I controlled substance. Schedule I substances are considered to have […]
Horror Retail Meets Copyright Law
Policing your trademarks is as important as registering them. Policing requires that the trademark and other rights owners monitor the world of commerce to ensure that others are not stealing their intellectual property and, if so, take immediate action against infringers. Many corporations zealously defend their trademark portfolios. Here’s but one example. In a recent article at Wired.com, The […]
Why Perform a Trademark Search?
It is surprising how many trademark applicants file their applications without having performed a search to see whether their proposed trademark is even registrable. If you fall into this category, here is some guidance. Once you have created a list of potential trademarks, you have to ensure that no one else has registered the mark […]
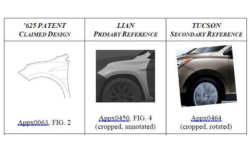
Major Change for Designers and Design Patent Owners
Did You Feel It? The Earth Just Shifted Under Every Designer and Design Patent Owner. In March and April, we reminded you that there are two types of patents – utility and design. Utility patents address how the better mousetrap catches mice. Design patents address the ornamental appearance of the mousetrap. Our topic this month is again design patents. […]
Welcome Gretchen L. Temeles, Ph.D., J.D.
A new lawyer has joined the ranks of Lipton, Weinberger & Husick. So, welcome our new partner, Gretchen L. Temeles, Ph.D., J.D. Gretchen arrives at our firm with experience that will greatly complement our patent prosecution and related practice. Here’s an overview of her experience: Gretchen is an experienced intellectual property attorney and scientist. She […]